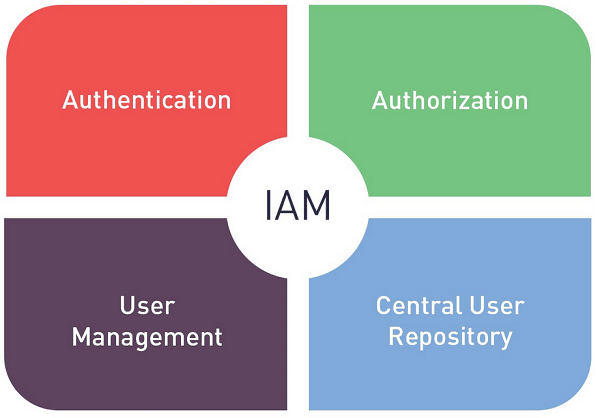
Identity & access management (IAM) software help businesses manage access to companies’ internal data & resources within employees to safeguard critical information.
Every company’s online appearance is centred on security, and every company’s network management strategy is built around it. They must constantly be aware of who is using their digital resources.
Therefore, it is in their best advantage to use every option at their disposal, whether it be software, hardware, or service, to protect the security of their networks and data. Among these possibilities, using Identity Access Management (IAM) solutions is one of the best ways to guarantee network security.
Top 5 IAM software
- Okta
- RSA SecurID
- Ping Identity
- Jump Cloud
- Idaptive Next-Gen Access
IAM Meaning
IAM is a framework of policies and technologies for ensuring that the right individuals have access to the right resources at the right times and for the right reasons. In the context of businesses, IAM helps to protect sensitive information and resources by managing and controlling access to them.
This can include tasks such as creating and managing user accounts, setting access controls and permissions, and monitoring and auditing user activity.
IAM solutions can be implemented on-premises or in the cloud and can include a variety of different tools and technologies, such as authentication and authorization systems, single sign-on, and identity and access governance.
Meaning of IAM software
Tools for managing access rights to sensitive data and resources are known as the IAM platform. IAM software that companies can utilize includes:
- Authentication and Authorization Systems: Systems for user authentication and authorization are employed to confirm users’ identities and ascertain if they are authorized to access particular resources. Multi-factor authentication (MFA), password management, and identity federation are a few examples.
- Single Sign-On (SSO): Instead of having to remember and input different login credentials for each application or system, single sign-on (SSO) enables users to access various applications and systems with a single set of login credentials. Examples of SSO solutions that offer SSO services include Okta, OneLogin, and Auth0.
- Identity and Access Governance: Access Governance systems assist organisations in managing and monitoring access to resources. They do this by establishing and enforcing access controls, keeping an eye on user behaviour, and creating reports on compliance and access. Examples of IAG solutions include SailPoint, CyberArk, and Saviynt.
- Identity and Access Management (IAM) as a Service (IDaaS): These cloud-based IAM solutions give companies access to a variety of IAM services, including authentication, authorization, and access governance, without the need to manage and maintain the infrastructure on-premises.
Examples of IDaaS solutions include Microsoft Azure Active Directory, AWS and Access Management (IAM), and Google Cloud Identity. - Identity and Access Management Platforms: These platforms provide a comprehensive set of tools and features for managing and controlling access to resources, including authentication, authorization, access governance, and identity management. Examples include Oracle Identity Governance, & IBM Security Identity Manager.
These are just a few examples of the many different types of IAM tools that businesses can use to protect sensitive information and resources. The specific tools and solutions that a business chooses will depend on its unique needs and requirements.
Why should businesses use IAM platforms
Businesses should use IAM platforms to protect sensitive information and resources by managing and controlling user access to them. IAM tools provide businesses with a range of benefits including:
- Improved security
- Compliance
- Increased efficiency
- Improved User Experience
- Cost reduction
Overall, IAM tools provide businesses with the ability to protect sensitive information and resources, meet regulatory requirements, increase efficiency, improve user experience and reduce costs.
Top 5 IAM Tools: Features, Pricing, Ratings, Pros, Cons & More
Okta
In terms of access control, authentication, and single sign-on, Okta has long held the top spot. Okta provides users with a straightforward and manageable SaaS-based method for implementing IAM without a lot of complexity.
The product has several authentication choices, including multi-factor, single sign-on, and biometric, and behavioural tracking is a bonus. One of the simplest routes to sophisticated identity management is with Okta.

Okta Features
- Compliance, Account, Role, Access Request & Password Management
- Multi-factor Authentication
- User Activity Monitoring
- Single Sign-On (SSO)
- API Access Management
Okta Pricing
- Okta offers a free trial. The free trial includes 7000+ pre-built integrations, No vendor lock-ins, All your users, groups, and devices in one place, & Automated 1-click user onboarding and offboarding.
- The pricing for Workforce Identity Products plans starts at $2 per month/per user & goes up to $11 per user/per month. Plans after $4 offer between 50 workflows to unlimited workflows. The Advanced Server Access starts at $15 per server/per month.
- The Customer Identity Cloud has three major plans, enterprise, B2B & B2C. The pricing for enterprise-level plans is quotation based, for the B2B plan the pricing ranges between $23 to $240, & B2C plan pricing ranges between $130 to $800.
For Detailed pricing, visit Okta pricing page.
Okta Pros & Cons
| Pros 👍 | Cons 👎 |
|---|---|
| Fast & Responsive | Lack of customization |
| Instant notification | Less responsive |
| Responsive customer support | Buggy mobile app |
SpotSaaS has rated Okta 9.8 out of 10. Check out- Here
RSA SecurID
Multi-factor authentication (MFA) technology like RSA SecurID is employed to safeguard network resources including software and websites. Its goal is to minimise risk and uphold compliance without interfering with worker productivity.
By verifying user identities, this technology may make sure that users are only given access to the resources they require to perform their duties. RSA SecurID can swiftly and securely grant authorised access to both on-premises and cloud-based services.
RSA SecurID Features
- Compliance Management
- Access Request Management
- Account Management
- Password Management
- Multi-factor Authentication
- Role Management
- User Activity Monitoring
- Single Sign-On (SSO)
- Passwordless Login
- API Access Management
RSA SecurID Pricing
- A Free Trial is available for RSA SecurID for 2 weeks- users can avail cloud multi-factor authentication (MFA) solution.
- The paid plans are quotation based & company’s’ sales team is to be contacted for the same.
For Detailed pricing, visit RSA SecurID pricing page.
RSA SecurID Pros & Cons
| Pros | Cons |
|---|---|
| Simple to use | Lacks a physical device providing codes |
| Very secure | Takes time to load security code |
| Good support team |
SpotSaaS has rated RSA SecurID 8.9 out of 10. Check out- Here
Ping Identity
In order to manage and give secure access to mobile, cloud, and on-premise apps, external and internal networks, and APIs, enterprises can use the identity and access management tool Ping Identity. To ensure compliance with statutory restrictions, the platform automatically recognises and stops abnormal actions using artificial intelligence (AI) technology.
It enables businesses to create unique rules that guarantee secure access to resources and collect, synchronise, and archive data from several sources in a single location for later use. Numerous device management options, two-factor authentication, single sign-on (SSO), data governance, customised templates, API access, geo-fencing, and other features are available.
Additionally, administrators can add users, design unique workflows to manage registration and authentication requests, and define products and deployment settings.
Ping Identity Features
- Advanced cloud identity solution
- Simplify IAM while minimising costs
- Accelerate time to value
- Comply with regulations
- Architected for enterprise hybrid IT
Ping Identity Pricing
- Users can try the software for Free during the Free Trial period. However, there is a paid version as well by Workforce360.
- Workforce360 paid plan offers features like authentication & single sign-on, adaptive multi-factor authentication, & directory data storage at $5 per user/per month.
For Detailed pricing, visit Ping Identity pricing page.
Ping Identity Pros & Cons
| Pros | Cons |
|---|---|
| Operates even without network | Complex role management and entitlement creation |
| Multi-factor authentication | Synchronisation lags |
| High security | Buggy mobile app |
SpotSaaS has rated Ping Identity 9.0 out of 10. Check out- Here
Keycloak
With an emphasis on contemporary applications including single-page applications, mobile applications, and REST APIs, Keycloak is an open-source identity and access management platform.
Keycloak offers a wide range of services, including fully configurable login screens, password recovery, accepting agreements, and more. Without any scripting at all, your application may quickly integrate all of these Keycloak functionalities. By giving Keycloak control over the user’s authentication, you may relax about authentication procedures, securely store passwords, etc.
Without needing to modify the programme, you may enable two-factor authentication. This improves the security of your application as in this case it cannot access user credentials; instead, it can only access tokens that Keycloak has issued.
Keycloak Features
- Multiple Protocols Support
- SSO
- Admin Console
- User Identity and Accesses
- External Identity Source Sync
- Identity Brokering
- Social Identity Providers
- Pages Customization
Keycloak Pricing
Keycloak does not offer a Free plan & the recurring cost is quotation based. Users can connect with their sales team to get the best quote as per requirements.
For Detailed pricing, visit Keycloak pricing page.
Keycloak Pros & Cons
| Pros | Cons |
|---|---|
| Ease of Implementation | No free trial |
| Open-source platform | Not very strong customer support |
| Secure tool | Multitenancy and High-Availability configuration and monitoring could be better |
SpotSaaS has rated Keycloak 8.6 out of 10. Check out- Here
Idaptive Next-Gen Access
In order to safeguard businesses from unwanted data access, cyberattacks, and data breaches, Idaptive offers Next-Gen Access solutions. Each user’s access is controlled using a Zero Trust and Security First approach by validating their devices and confirming their identities. Before any access to apps is permitted, a second layer of security is created by multi-factor authentication.
To assign risk ratings to each accessible event, the programme can monitor the network, the device, and understand user behaviour context. Idaptive eliminates the need for passwords by securely authenticating each access with a variety of supporting factors, such as FIDO2 keys, virtual and hardware tokens, etc.
Idaptive Next-Gen Access Features:
- API Access, Compliance, Access Request, Password, Role Management
- Passwordless Login
- Single Sign-On (SSO)
- User Activity Monitoring
- Multi-factor Authentication
Idaptive Next-Gen Access Pricing
Idaptive Next-Gen Access offers a Free Trial option to users. The paid plans are divided in 4 categories, such as:
- Single-sign-on plan starts at $2 per user/per month & goes up to $4 per user/per month- for standard SSO & Adaptive SSO.
- Multi-factor authentication plan starts at $2.50 per user/per month and gies up to $5 per user/per month for standard & adaptive MFA.
- Lifecycle management plan starts at $3.50 per user/per month & goes up to $7 per user/per month.
- The mobile devices plan starts at $2 per user/per month & goes up to $9 per user/per month.
For Detailed pricing, visit Idaptive Next-Gen pricing page.
Idaptive Next-Gen Access Pros & Cons
| Pros | Cons |
|---|---|
| Great password management system. | Lack of section management |
| Easy to implement. | High maintenance & updates |
| Multiple features for safety |
SpotSaaS has rated Idaptive Next-Gen Access 8.9 out of 10. Check out- Here
Conclusion
Overview of the top 5 IAM tools
| IAM Tool Name | Spot Score | Free Trial | Pricing |
|---|---|---|---|
| Okta | 9.8/10 | Yes | Starts at $2 & goes up to $800 |
| RSA SecurID | 8.9/10 | Yes | Quotation Based |
| Ping Identity | 9.0/10 | Yes | Price goes up to $5 |
| Keycloak | 8.6/10 | No | Quotation Based |
| Idaptive Next-Gen Access: | 8.9/10 | Yes | Starts at $2 & goes up to $9 |
In conclusion, IAM is a crucial aspect of maintaining the security and integrity of any organization. By implementing the right tools, companies can effectively control and monitor access to their systems and data, while also ensuring compliance with industry regulations.
The top 5 IAM tools discussed in this blog, Okta, RSA SecurID, Ping Identity, Keycloak, & Idaptive Next-Gen Access each offer unique features and capabilities that can meet the specific needs of any organization. It is important to carefully evaluate the options and choose the tool that best fits your organization’s requirements.
Adopting a robust identity and access management solution not only provides security but also improves productivity, compliance and overall efficiency of the organization.
If you also want to deep dive into the world of IAM and learn about its benefits & risks, here is a detailed blog on the same by team SpotSaaS:
Introduction to IAM- Identity and Access Management Tools: A Comprehensive Guide (2023)
Read More
Resource Management Software: A detailed guide on how to use
How SaaS Is Redefining Cybersecurity
What is the IAM tool?
Tools for managing access rights to sensitive data and resources are known as the IAM tools. Some examples are:
1-Authentication and Authorization Systems
2-Single Sign-On (SSO)
3-Identity and Access Governance
4-Identity and Access Management (IAM) as a Service (IDaaS)
5-Identity and Access Management Platforms
What are the five pillars of IAM?
The five pillars of IAM include:
1- Lifecycle and governance
2- Federation- single sign-on and multi-factor authentication
3- Network access control
4- Privileged account management
5- Key encryption
Do IAM Software offer Free Trial?
Yes, many IAM software like Okta & Ping Identity offer Free Trail for first time users.