In today’s world, keeping your online connections safe is more crucial than ever. Tailscale emerges as a powerful ally, built on the robust foundation of Wireguard® mesh VPN technology.
This guide will illuminate how Tailscale VPN streamlines secure networking with ease and flexibility. Dive in to unlock seamless protection for your digital landscape.
Key Takeaways
- Tailscale, founded in 2019 by former Google engineers, revolutionizes secure networking with their user-friendly mesh VPN technology based on Wireguard®.
- With features like secure remote database access, granular network segmentation, and over 100 integrations, Tailscale provides a robust solution for both enterprises and personal use.
- Tailored for the modern digital landscape, Tailscale is trusted by over 4,000 companies to safeguard their operations using encrypted point-to-point connections without complex setups.
- The service offers strong security measures such as least privilege enforcement and real-time audit log streaming that enhance safe online working environments for teams worldwide.
- Getting started with Tailscale is simple—download the app, create an account, set up devices quickly—and they offer a free trial to experience how straightforward it is to establish a secure network.
Understanding Tailscale VPN Service
Tailscale is a company that offers secure networking solutions for businesses and individuals. Their service provides seamless, zero-config VPN capabilities to ensure secure remote access to databases and resources.
Brief Overview of Tailscale Company
Based in the tech-savvy city of Toronto, Canada, Tailscale Inc. is a relatively new name making big waves since its inception in 2019. It’s not every day you see a startup co-founded by former Google engineers Avery Pennarun, David Crawshaw, David Carney, and Brad Fitzpatrick—experts who know a thing or two about creating robust networking solutions.
The team set out to simplify secure networks with their innovative software-defined mesh VPN.
What sets Tailscale apart is its laser focus on user-friendliness without sacrificing security. They’ve secured considerable investment to tune of $112 million within just three years—a testament to their vision and potential impact on remote access technology across platforms like Linux and Android apps.
Their service leverages open-source technologies coupled with carrier-grade NAT traversal capabilities to revolutionize how we think about private networks and firewalls. With the ease-of-use of an Android app and the reliability needed for enterprise-level tasks, they’re rapidly becoming the go-to solution for seamless connectivity challenges faced by companies worldwide.
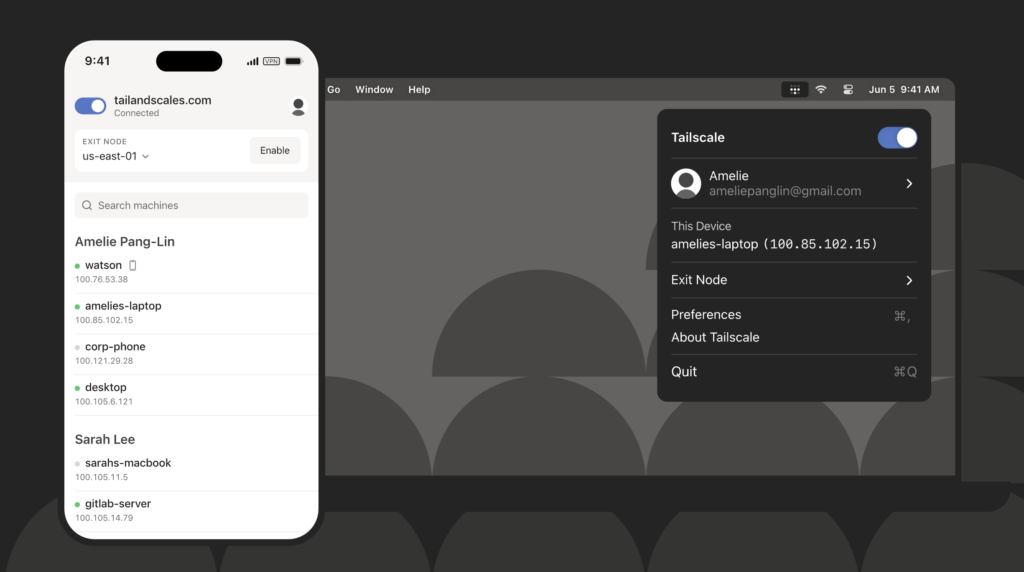
Tailscale VPN Service
Tailscale steps up the game in secure networking with a suite of services that simplifies connectivity. Their emphasis on both security and user-friendliness makes them standout providers of mesh VPN technology.
| Feature | Description |
|---|---|
| Secure Remote Database Access | Users can securely access their databases from anywhere, thanks to Tailscale’s point-to-point networking. This approach ensures that only people with the right permissions can connect, maintaining a high level of security. |
| Granular Network Segmentation | By offering detailed network segmentation, Tailscale enables safe interactions between resources. You can connect various environments like clouds and on-premises networks without exposing firewall ports. |
| Least Privilege Enforcement | The principle of least privilege is at the core of Tailscale’s philosophy. Users have precisely the access they need – nothing more, nothing less – which greatly reduces risk profiles. |
| Automated User Onboarding | For enterprises, setting up new team members is hassle-free. The automated onboarding process gets employees connected and ready to work securely in no time. |
| SSH Session Recording | Keeping track of who does what is critical for security. With SSH session recording, Tailscale provides an additional layer of oversight and accountability. |
| Audit Log Streaming | Real-time streaming of audit logs aids compliance and monitoring efforts within organizations. This feature helps identify potential security threats or operational anomalies as they happen. |
| Over 100 Integrations | Compatibility with numerous workflows and operating systems is key to Tailscale’s enterprise appeal. Their support for over 100 integrations means seamless adoption into existing infrastructures. |
| Support for Various Operating Systems | With support for popular platforms like FreeBSD, OpenBSD, and more, Tailscale ensures that your secure network stretches across all necessary devices and systems. |
The Importance of Secure Networking
Secure networking is crucial for businesses and individuals alike, especially when it comes to accessing sensitive databases and maintaining privacy. With Tailscale’s track record of being trusted by over 4,000 companies, it’s clear that their technology offers a secure solution for remote access and communication.
Secure, Remote Access to Databases
Accessing databases from anywhere has never been safer thanks to Tailscale. With their cutting-edge mesh VPN technology, your remote database connection is as secure as if you were hooked up to the office’s Wi-Fi, but with the freedom to work from any location.
Imagine seamlessly managing your SVN repository or pushing code through GitHub Desktop without ever worrying about unauthorized snooping or data breaches.
Tailscale stands out by making sure only the right people can reach sensitive information in your databases. It’s a game-changer for teams that require strict privacy controls and secure access protocols.
They enforce least privilege network connectivity, so you’re assured each team member gets precisely what they need — no more, no less. This means whether you’re updating packages using CLI tools or reviewing commits in Xcode, Tailscale keeps these connections tightly locked down while maintaining simplicity and efficiency.
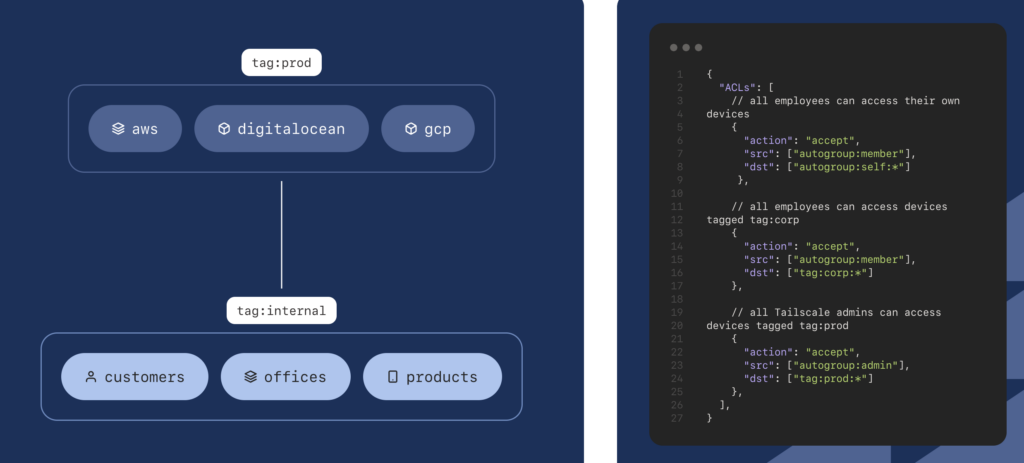
Trusted by 4,000+ Companies
Secure, remote access to databases is crucial for businesses, and Tailscale has earned the trust of over 4,000 companies in providing this essential service. As a reliable choice for secure networking, Tailscale offers trusted automated user onboarding, SSH session recording, and audit log streaming.
This widespread adoption speaks to the reputation and effectiveness of Tailscale’s solutions in meeting the security needs of a diverse range of organizations.
Tailscale leverages its industry-leading technology to provide seamless integration into existing workflows while ensuring that data remains protected. By simplifying secure network connectivity with zero-config VPN and site-to-site networking capabilities, Tailscale offers peace of mind to thousands of companies seeking robust security solutions.
Check more Top 10 VPN Software in 2023
Key Features of Tailscale VPN
Tailscale offers a zero-config, no-fuss VPN that simplifies secure networking for businesses and individuals. With site-to-site networking and integrations for various workflows, Tailscale provides a seamless and efficient solution for secure connectivity.
Zero-Config, No-Fuss VPN
Tailscale offers a zero-config, no-fuss VPN solution. With Tailscale, there’s no need to navigate complex setups or configurations. This hassle-free approach allows you to establish secure, remote access to databases with ease.
Plus, Tailscale enforces least privilege and provides granular network segmentation for secure resource access without the need for extensive configuration.
Furthermore, Tailscale eliminates the hassle of opening firewall ports by offering seamless site-to-site networking that connects clouds, VPCs, and on-premises networks effortlessly.
Site-to-Site Networking
Tailscale’s site-to-site networking feature securely connects multiple networks, including clouds, VPCs, and on-premises networks without the need to open firewall ports. This capability ensures seamless communication between different locations while maintaining privacy and security.
Enterprises can leverage Tailscale’s mesh VPN technology to establish a reliable and encrypted network between their various sites, enhancing overall connectivity and data protection.
With Tailscale’s site-to-site networking, companies can effortlessly integrate diverse environments without compromising security or dealing with complex configurations. This empowers organizations to streamline their operations while ensuring that sensitive data remains protected across their entire network infrastructure.
Integrations for Various Workflows
Tailscale provides an extensive range of integrations for diverse workflows, enabling seamless operation across different systems and platforms. These integrations streamline operational processes and enhance productivity through tailored solutions that cater to specific business needs.
| Integration | Description |
|---|---|
| GitOps Integration | Tailscale seamlessly integrates with GitOps tools, facilitating version control and continuous deployment in a secure network environment, streamlining development, testing, and deployment workflows. |
| Wi-Fi Network Integration | Tailscale’s integration with Wi-Fi networks ensures secure connectivity and seamless access to resources across various wireless environments, providing reliable performance and enhanced mobility for users. |
| Site-to-Site Networking Integration | Tailscale integrates with site-to-site networking solutions to foster secure communication between multiple locations, enabling efficient sharing of resources and information across geographically distributed networks. |
| Flexibility across Operating Systems | Tailscale offers integrations across a wide array of operating systems, including Windows, macOS, Linux, iOS, and Android, ensuring consistent user experiences and unified management across different devices. |
| Exit Node Configuration | The integration of exit node configuration within Tailscale allows organizations to fine-tune traffic routing based on specific requirements or preferences, optimizing network performance and resource utilization. |
| 100+ Workflow Integrations | Tailscale provides over 100 integrations tailored to meet the specific needs of various workflows and operating systems, ensuring seamless interoperability with popular applications used in diverse business environments. |
Tailscale for Enterprise
Tailscale for Enterprise offers improved security and flexibility, allowing businesses to integrate it seamlessly into their existing workflows. With Tailscale, companies can ensure secure remote access and enhanced connectivity for their employees.
Improved Security
Tailscale for enterprise provides robust security measures, ensuring that sensitive data and resources are protected from unauthorized access. With granular network segmentation and automated user onboarding, Tailscale offers an advanced level of control over who can access what within the network.
Additionally, SSH session recording and audit log streaming provide enhanced visibility into network activities, allowing for proactive monitoring and threat detection to maintain a secure networking environment.
By leveraging Wireguard®, a highly secure VPN protocol, Tailscale ensures encrypted communication channels between devices, safeguarding against potential cyber threats. This commitment to security aligns with the growing need for reliable remote access solutions in today’s digital landscape while providing peace of mind to organizations looking to fortify their network infrastructure.
Check more Top 5 Remote Monitoring And Management Software For IT Teams
Flexibility and Integration into Existing Workflows
Tailscale offers unparalleled flexibility and seamless integration into existing workflows, making it a top choice for companies looking to streamline their networking solutions. With over 100 integrations compatible with various workflows and operating systems, Tailscale simplifies the process of incorporating VPN technology into your current setup.
This level of adaptability means that you can effortlessly integrate Tailscale into your established infrastructure without disrupting daily operations, ensuring a smooth transition to enhanced security and connectivity.
Furthermore, Tailscale’s advanced features are designed to seamlessly complement existing workflows. Whether it’s site-to-site networking or automated user onboarding for enterprise use, Tailscale provides a comprehensive solution that harmonizes with your organization’s unique processes while enhancing overall efficiency and security.
Tailscale for Personal Use (Homelab)
TailScale is perfect for personal use, providing simple, reliable, and powerful networking solutions. Our commitment to security ensures that your home network remains protected at all times.
Simple, Reliable, and Powerful
Tailscale offers a simple, reliable, and powerful solution for secure networking. Its user-friendly interface enables easy management of devices and network configurations from anywhere.
The scalability of Tailscale makes it an ideal choice for both personal and enterprise use, offering the same level of simplicity, reliability, and power across the board.
With Tailscale’s commitment to security and its encryption technology, users can trust that their data is protected as it travels through the secure mesh network. Additionally, Tailscale’s versatility allows for seamless integration into existing workflows whether for personal homelab use or within enterprise environments.
Commitment to Security
Tailscale’s commitment to security is unwavering. With its foundation in Wireguard® technology, Tailscale offers robust encryption and secure mesh networking, ensuring that every connection is protected against unauthorized access.
The platform also provides granular network segmentation for controlled resource access, adding an extra layer of defense to your network. Tailscale understands the importance of safeguarding sensitive data and provides automated user onboarding, SSH session recording, and audit log streaming for enterprise users, ensuring a comprehensive approach to security.
Small businesses as well as large enterprises can rely on Tailscale’s unwavering dedication to security in every aspect of their networking needs – from secure remote database access to seamless integrations into existing workflows.
With Tailscale’s commitment at the core of their platform, customers can trust that their networks are fortified with the highest standards of protection against evolving cyber threats.
Getting Started with Tailscale
To get started with Tailscale, simply follow our quickstart guide and try it for free. With our easy setup process, you can start enjoying the benefits of secure networking in no time.
Tailscale Quickstart Guide
Tailscale offers a straightforward process to get started with their secure networking solution. Follow the steps below to quickly set up and begin using Tailscale:
| Step | Description |
|---|---|
| Downloading and Installing Tailscale | Begin by downloading and installing the Tailscale client on your device or server. The process is quick and easy, ensuring that you can get started with secure networking without any hassle. |
| Creating an Account | Once installed, create an account on the Tailscale website. This will allow you to manage your network and access various features offered by Tailscale. |
| Setting up Devices | After creating an account, proceed to set up the devices that you want to connect securely through Tailscale. This step involves adding devices to your network and configuring their permissions, allowing for seamless connectivity. |
| Integrating Workflows | Take advantage of Tailscale’s 100+ integrations for different workflows and operating systems to further enhance the functionality of your secure network. Easily integrate with various applications and systems to streamline your operations. |
| Securing Remote Access | Utilize Tailscale’s capabilities to ensure secure, remote access to databases or other resources within your network. With Tailscale, you can trust that your access is encrypted and authenticated for enhanced security. |
| Enabling Site-to-Site Networking | Benefit from site-to-site networking that connects clouds, VPCs, and on-premises networks without compromising security by opening firewall ports. |
| Enjoying Ease of Use | Experience the simplicity of setting up a secure mesh network with Tailscale’s zero-config approach, eliminating the need for complex VPN configurations while providing robust security measures at every step. |
| Leveraging Wireguard® Technology | Take advantage of the advanced security features underpinning Tailscale, which is built on Wireguard® technology known for its strong encryption and efficient performance. |
Trying Tailscale for Free
Get started with Tailscale’s free trial to experience seamless and secure networking. Simply sign up, download the app, and connect your devices within minutes. Experience the convenience of a zero-config, no-fuss VPN that provides trusted and encrypted access to your databases from anywhere.
With Tailscale, you can install it on various devices such as iPhones, Linux servers, Macs, robots, and home network machines effortlessly. The quick and easy setup allows for immediate integration into your existing workflows without any hassle or complex configurations.
Conclusion
In conclusion, embracing Tailscale’s mesh VPN technology enables secure, remote access to databases and robust site-to-site networking. It empowers both enterprises and individuals with simplified but powerful network security solutions.
Tailscale’s no-fuss VPN features cater to the demands of a fast-paced world, rendering it an essential tool for creating encrypted mesh networks effortlessly. With its seamless integrations and emphasis on security, Tailscale stands as a game-changer in the realm of secure networking by default.
(Image Credit: Tailscale)
Frequently Asked Questions
What is Mesh VPN Technology, and How does Tailscale use it?
Mesh VPN technology creates a secure network that connects multiple devices directly. Tailscale uses this innovative approach to ensure seamless and safe wifi connections regardless of location.
Can Tailscale protect all my devices?
Yes, with Tailscale’s comprehensive guide, you’ll learn to safeguard various devices, creating a dependable shield for your personal and work-related wifi needs.
Is setting up Tailscale complicated?
Not at all! You’ll find the setup process straightforward thanks to detailed instructions aimed at making secure networking user-friendly for everyone.
Will using Mesh VPN through Tailscale slow down my internet speed?
Experience rapid connectivity without compromise; TailScale’s mesh VPN technology is designed to deliver secure and efficient performance across your entire wifi network.