
Welcome to the kingdom of efficiency, where business operations are optimized by an effective Identity and Access Management (IAM) strategy that rules supreme!
Say goodbye to labour-intensive, error-prone manual chores and embrace safe, automated, and intelligent procedures. In this article, we’ll explore the benefits of an IAM strategy and see how it can elevate your company’s operations to the next level of efficiency. So buckle up and let’s embark on this quest towards streamlining success with IAM Strategy
The security field known as identity and access management deals with the control of digital identities, including their authentication, authorisation, and access to resources throughout a technology infrastructure.
Based on a person’s position and duties inside an organization, IAM offers a centralized approach for managing and regulating access to resources, systems, and applications. IAM aims to facilitate user access to the resources they require to carry out their work while simultaneously ensuring that only authorized personnel to have access to sensitive data and systems.
Learn more about IAM, IAM Strategy & the best technology in the domain here –
The 5 Top Identity and Access Management Tools
Introduction to IAM- Identity and Access Management Tools: A Comprehensive Guide
Components of business processes IAM software can manage
The following business process elements can be handled by cloud-based Identity verification and Access Management tools:
- User Authentication: User Authentication can be managed by IAM technologies by offering safe ways for users to validate their identities to gain access, such as single sign-on, multi-factor authentication, and password-less authentication.
- Authorization: IAM technologies can control authorization by identifying the resources that a person is permitted access to based on their assigned roles, responsibilities, and privileges within an organization.
- User Management: To facilitate efficient authorization and authentication, IAM technologies can handle user information such as personal particulars, contact information, and group membership.
- Access Management: IAM technologies can regulate who has access to what and under what circumstances by using access management to manage access to resources.
- Identity Federation: IAM tools may offer identity federation, which enables users to access resources from several organizations using a single set of credentials.
- Compliance: By offering a thorough view of user access and behaviour, this technology can assist firms in complying with rules and standards like GDPR and HIPAA as per organizations’ need.
- Reporting: IAM technologies can assist organizations to identify who is accessing what resources, when, and for what purposes by offering reporting and auditing capabilities through automation.
Let’s explore the ways in which a robust IAM strategy can optimize your company’s operations and propel you towards digital success
Identity and Access Management is a critical aspects of modern-day businesses, particularly in the digital era. With the increasing number of cyber threats and data breaches, organizations are seeking ways to secure their sensitive information and ensure that only authorized individuals have access to it.
Implementing an effective IAM system can not only enhance the security of an organization but also streamline business processes by automating repetitive tasks, reducing manual errors, and enabling secure collaboration among employees, partners, and customers.
Here, we will explore how IAM Strategy can improve business processes in the digital era and help organizations achieve their goals efficiently and securely:
1- Automated user provisioning
By automating the process of creating, updating, and removing user accounts, automated user provisioning with IAM software aids in streamlining corporate processes. By doing so, the labour-intensive manual procedure of setting up and managing user accounts is eliminated.
When a new employee enters the company, the identity management software can automatically create their user account and provision the required access to systems and apps based on predetermined rules. This is known as automated user provisioning.
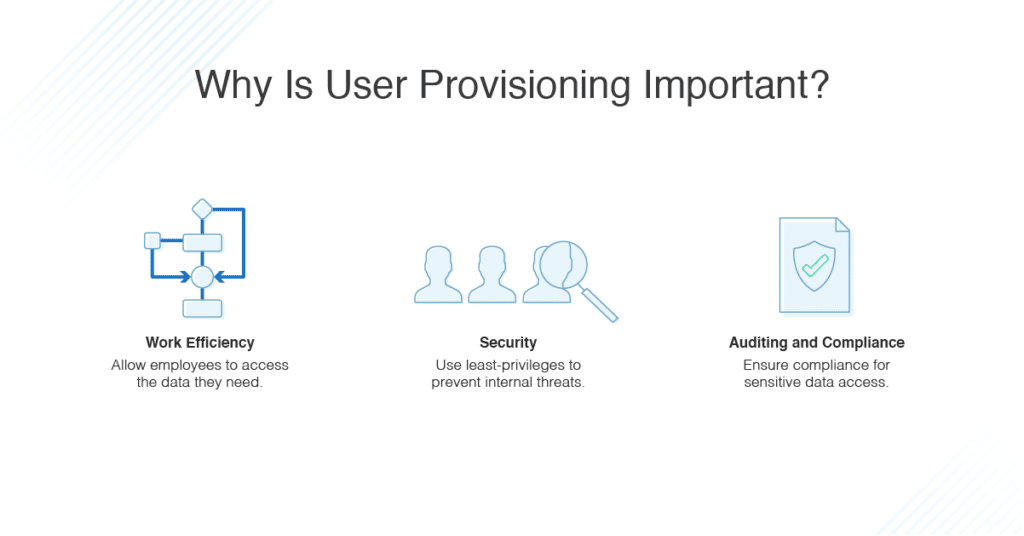
The risk of security breaches can be decreased by using the access and identity management system to automatically deactivate accounts and remove access when an employee leaves the company.
Additionally, the IAM software may automatically update a user’s access to reflect a change in an employee’s function within the company, ensuring that they have the proper access to systems and apps. This shortens the time and effort needed to manually manage user accounts while streamlining the process of managing user access.
Overall, IAM software’s automatic user provisioning makes it easier to manage user accounts and access, which frees up companies to concentrate on more strategic projects and lessens the administrative strain on IT.
2- Centralized access control
Centralized access control with Identity and Access Management tools helps businesses to maintain security, and compliance & allows scalability. It also enables businesses to stay efficient through:
Businesses may automate the process of granting and revoking user access by using IAM tools, which lessens the strain on IT employees and allows them to concentrate on other crucial responsibilities. As the IAM system will enforce the organization’s access control policies, this can also lower the possibility of human error while granting access.
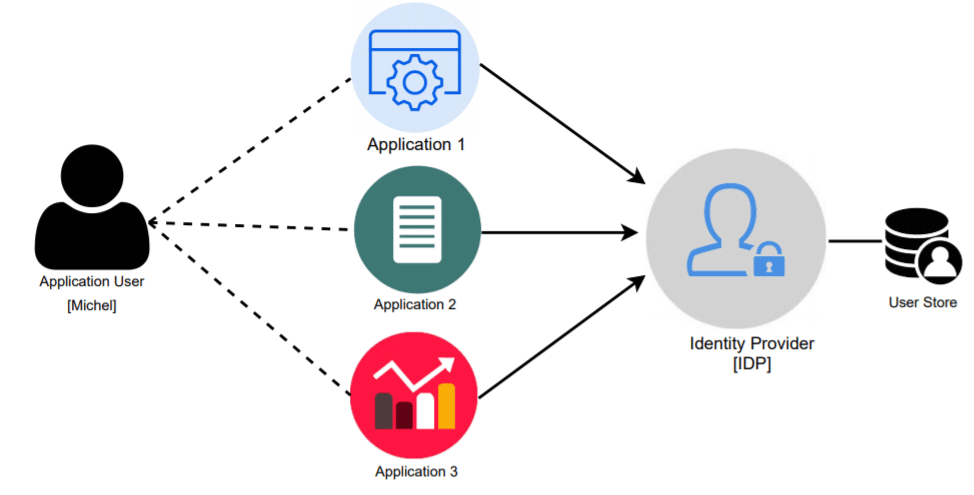
Overall, centralized access control with IAM tools provides businesses with a secure and efficient way to manage user identities and their access to company resources, helping to reduce the risk of security breaches and improve compliance with industry regulations, all while ensuring efficiency.
3- Single Sign-On (SSO)
Single Sign-On (SSO) with Identity and Access Management helps businesses work more efficiently in several ways:
- User Convenience: With SSO, users only need to remember a single set of login credentials to access all of their applications and systems.
- Increased Productivity: SSO can increase productivity by minimizing the time and effort needed to log in to several systems. This allows users to concentrate on their job rather than managing multiple login credentials.
- Increased Security: SSO helps increase security by reducing the number of passwords that users need to remember.
- Centralized Management: With SSO, administrators can manage user access to all systems from a single, centralized location.
- Improved User Experience: SSO helps improve the user experience by reducing the number of login steps required to access different systems.
Let’s understand Single Sign-on Process as well from the below image.
Source – https://doubleoctopus.com/security-wiki/federation-and-sso/single-sign-on/
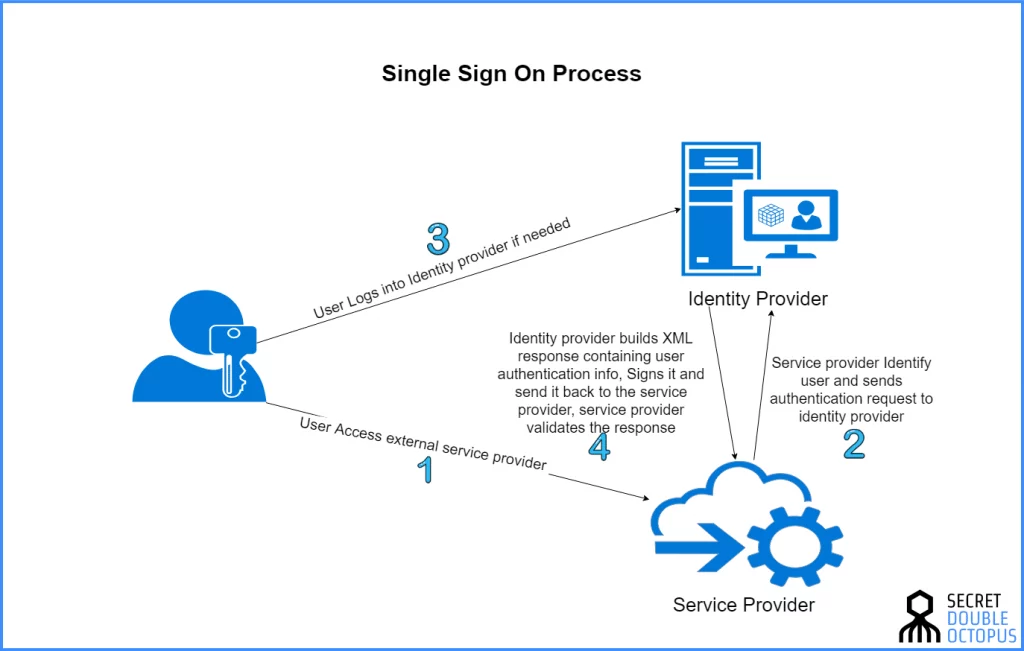
Overall, SSO with IAM increases productivity for enterprises by lowering the time and effort needed to log into various systems, enhancing security, and simplifying the management of user access to resources. This could assist boost output, enhance user contentment, and improve the user experience.
4- Automated compliance reporting
Automated compliance reporting with Identity and Access Management tools can help businesses stay efficient in several ways:
- Streamlined Compliance: The generation of compliance reports is automated by IAM tools, which lightens the workload of IT workers and allows them to concentrate on more crucial responsibilities.
- Consistent Reporting: Such systems offer a central location for managing user access and producing compliance reports, aiding in the maintenance of accurate and consistent reporting across the board.
- Improved Visibility: Such technologies give firms a thorough understanding of their compliance status by providing extensive reports on user behaviour and access.
- Easier Auditing: Auditing is made simpler thanks to automated compliance reporting provided by such tools because all pertinent data is centralized and readily available.
- Reduced Risk: Automated compliance reporting helps reduce the risk of non-compliance by providing real-time visibility into user activity and access.
By expediting the compliance reporting process, enhancing insight into compliance status, and lowering the risk of non-compliance, automated compliance reporting with IAM solutions can help businesses stay productive. This can assist firms in concentrating on their core competencies and more successfully achieving their compliance objectives.
5- Streamlined collaboration
Streamlined collaboration through Identity and Access Management (IAM) tools can help businesses stay efficient in several ways:
- Centralized User Management: Such tools deploy a centralized location for managing user identities and access rights to company resources, making it easier for administrators to manage and update stakeholder information.
- Improved Accessibility: By providing a centralized location for managing user access, IAM tools can help improve accessibility for stakeholders.
- Secure Sharing: Such tools can help secure collaboration by controlling access to shared resources and data.
- Improved Communication: Such tools can integrate with other collaboration tools, such as email and messaging platforms, making it easier for team members to communicate and collaborate.
- Efficient Workflows: Such tools can help streamline collaboration by automating agile workflows and processes, reducing the risk of delays and improving overall efficiency.
Overall, all these components can help ensure that users have the access they need to collaborate effectively, reducing the risk of delays and improving overall efficiency.
Conclusion
The key to maximizing the efficiency of your company processes is Identity and Access Management. IAM Strategy can make your company run more smoothly by streamlining user administration, enhancing security, automating compliance reporting, and promoting collaboration.
Therefore, it’s time to say goodbye to jumbled passwords, misplaced login information, and cumbersome processes and hello to safe and optimized corporate processes with IAM!
Consider it as a digital hand that will assist you in keeping everything in order in your company so you can concentrate on bigger and better things!
Read More
Efficiency with Contract Lifecycle Management (CLM) : Best Practices & Working
Improve customer engagement with marketing automation: 5 Unique Tips & Tricks!
Neglecting The IAM Process Is Fighting A Losing Battle To Achieve Operational Excellence
Frequently Asked Questions (FAQs)
What is IAM?
IAM stands for “Identity and Access Management.” It refers to the set of policies, procedures, and technologies that organizations use to manage digital identities and control access to their resources.
What is SSO & how does it work?
Single Sign-On (SSO) is a method of authentication that allows users to access multiple applications with a single set of login credentials.
The basic concept of SSO is that the user is prompted to log in once and the credentials are then verified and stored by a centralized authentication server. When the user wants to access a new application, the application redirects the user to the authentication server. If the user has already logged in, the authentication server returns an authentication token to the application, allowing the user to access it without having to re-enter their credentials.
How does IAM improve business processes?
IAM improves business processes by:
1- Automated user provisioning
2- Centralized access control
3- Single Sign-On (SSO)
4- Automated compliance reporting
5- Streamlined collaboration
Best IAM Tool In 2023?
Leading IAM tools to use in 2023 are:
Okta
Microsoft Azure Active Directory
Ping Identity
ForgeRock
AWS IAM



