Are you tired of feeling like a hamster on a wheel, constantly running around trying to keep track of all different passwords and manage access to data at your organization? It’s time to say goodbye to the chaos and hello to the world of identity and access management tools.
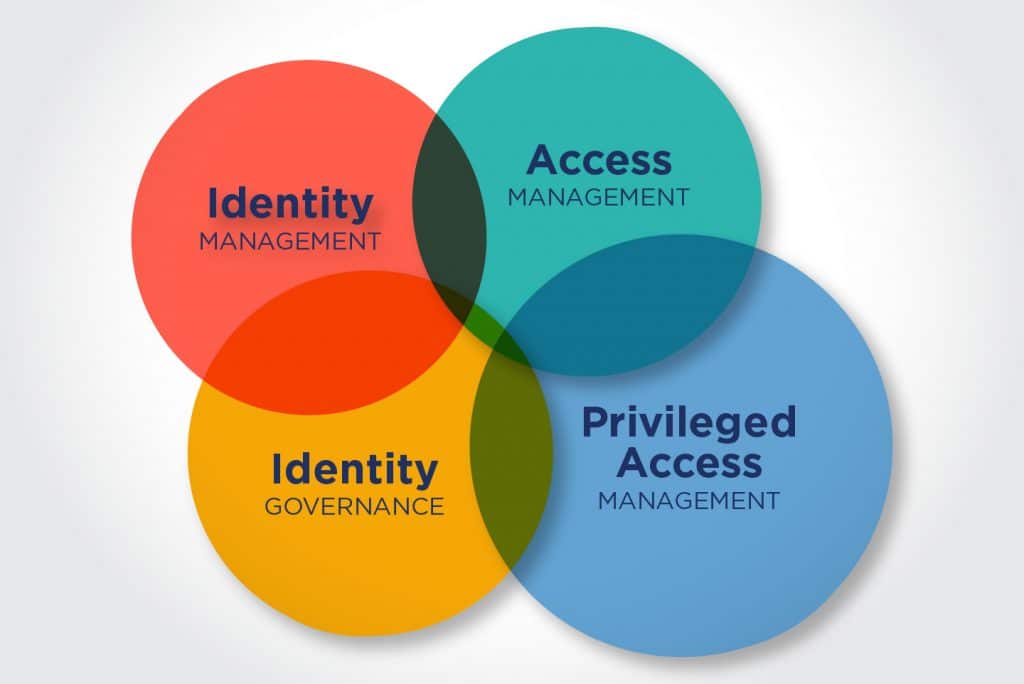
What Does Identity Access Management (IAM) Mean
In layman’s language, identity and Access Management (IAM) is a security practice that ensures the appropriate people have access to the right resources at the required times and for professional purposes.
It entails giving users an individual identification number and managing their access to resources including systems, networks, and data. This practice ensures that only authorized users have access to the tools they need to complete their jobs and that they can only use those tools for tasks they have been granted permission to perform.
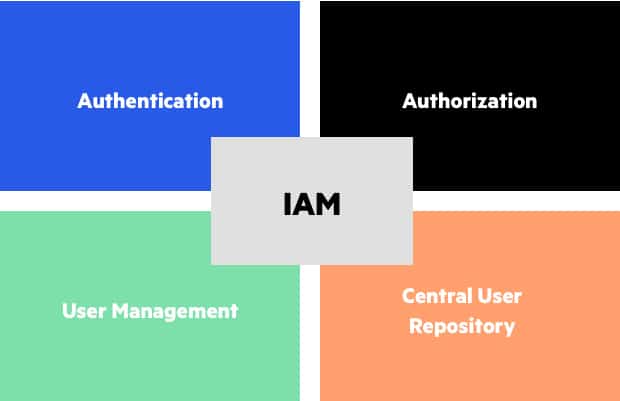
Tools for managing user identity, authentication, authorization, and privileges are frequently included in IAM systems, to guarantee that security regulations are being followed.
Importance & Benefits of Identity and Access Management
Globally, the IAM market is expected to grow to $34.52 billion by 2028, at a compound annual rate of 14.5% from 2021 to 2028. (Source)
For businesses in the digital age, Identity and Access Management Solutions are important & beneficial for a variety of reasons. Here are a few of them:
- Cloud Computing: Businesses these days rely on cloud services to manage resources & access. The work-from-home culture in the digital age has also promoted the usage of cloud technology. With the cloud, IAM is even more crucial to ensure the safety of data & resources.
- Mobile Services and Applications: Organisations now have to offer greater freedom to employees in terms of data accessibility via personal mobile phones while ensuring safety. With the right tool, this balance between increased accessibility & security can be achieved.
- Security: IAM solutions assist in making sure that only authorized users have access to the resources they need to execute their jobs. Such solutions also ensure that individuals can only access the precise resources and carry out the specific actions they are permitted to after the identity checks.
- Enhanced Productivity: IAM technologies can help to boost productivity and efficiency by giving users quick & easy access to the resources they need to conduct their tasks.
- Cost-Effectiveness: By automating many of the operations associated with managing user access, such as providing and de-provisioning user accounts and managing passwords, such systems can assist enterprises in lowering the cost of doing so.
Common Functions of IAM Tools- Identity Management
IAM software serves a variety of functions, some of the major ones are:
| User provisioning | Roles and permissions can be assigned to users, and user accounts can be created, updated, and deleted using IAM software. This ensures users have the required access to carry on their duties. It also assists in preventing illegal access to critical resources by identity verification. |
| Authentication | When users log in to an organisation’s systems and applications, IAM software can cross-check their identity. Several techniques, including passwords, biometric authentication, and two-factor authentication, can be used to accomplish identity verification, depending on the technology used. |
| Authorization | IAM software can be used to manage access to resources and actions individuals are permitted to take on those resources based on identity verification. Users can be given permission to accomplish this by assigning them, or rules-based access restrictions can be deployed. |
| Password Management | IAM software can be used for password management, which includes establishing password policies, enforcing password updates, and securely storing passwords, to ensure safety from data breaches. |
| Single sign-on (SSO) | IAM software can be used to let users log in to numerous systems and apps using a single set of credentials (single sign-on, or SSO) |
| Access governance | Using IAM software, you can monitor and audit user access to ensure it complies with security guidelines and rules. This may involve keeping track of who has used which resources and when and identifying and addressing possible security risks. |
| Reporting | To maintain compliance and evaluate security threats, IAM tools create reports following the majority of operations performed on the platform such as login time, systems accessed, and type of authentication. |
Components of IAM
IAM systems typically include several components, which may include:
- User Directories
- Authentication systems
- Authorization systems
- Password management systems
- Single sign-on (SSO) systems
- Access governance systems
In conclusion, Identity and Access Management are powerful as they help to simplify access right while ensuring secure access to your resources.
Implementing IAM
In 2022, more businesses shifted to a zero-trust IAM framework from conventional IT security protocols to secure their business resources. Businesses should take into account the following factors before making an investment in the IAM tool:
| Cost | Find out how much the IAM tool will cost, including any up-front or recurring charges and any training or support fees. |
| Scalability | Take into account whether the IAM tool can expand and adapt to your organisation. |
| Integration | Examine the tool’s compatibility with your current infrastructure and systems. |
| Security | Control access to a resource or data is a major function of the IAM product. Ensuring the IAM platform you choose for your business is secure enough is vital. |
| User experience | Take into account how simple it is for users to access resources and complete activities. |
| Support | Ascertain the tool’s degree of support, including the availability of tutorials, documentation, and customer service. |
| Flexibility | Take into account the tool’s adaptability, which includes the capability to modify permissions and policies to suit your particular requirements. |
| Compliance | Consider whether the IAM tool can help you comply with regulatory requirements if your company is subject to them. |
| Privileged Access | With the right IAM service, businesses must be able to manage access privileges to top management. While implementing access control, this must be considered. |
IAM Risks
Security lapses: The IAM software may be attacked by attackers if it is not properly configured or maintained, which could result in a security lapse.
Unauthorized access: If the IAM software is not used properly, it may enable unauthorised users to access confidential information.
Compliance violations: If the IAM software is not set up to comply with legal requirements, it may result in infractions.
User errors: When using the IAM programme, users may make mistakes, such as unintentionally providing excessive access or disclosing their login information.
User errors: When using the IAM programme, users may make mistakes, such as unintentionally providing excessive access or disclosing their login information.
Lack of training: If users are not given adequate instruction on how to use the IAM software, mistakes may be made and security problems may arise.
Top IAM Tools For Your Business
Okta
Okta is a management platform that secures critical resources for the workforce and customers.
The company’s identification is provided by Okta. Many of the largest businesses in the world connect their employees and safeguard them with the Okta Identity Cloud. Additionally, it securely links businesses with their partners, suppliers, and clients. The Okta Identity Cloud’s deep connections with more than 5,000 apps make accessing content from any device easy and secure.
By making the technology needed to complete their most important tasks safe and simple to use, Okta helps clients complete their goals more quickly through identity analysis.

Okta Features
- Compliance Management
- Access Request Management
- Account Management
- Password Management
- Multi-factor Authentication
- Role Management
- User Activity Monitoring
- Single Sign-On (SSO)
- Social Sign On
- Password-less Login
- API Access Management
- Integrate With Tools
Okta Pricing
Okta offers a free trial. The free trial includes 7000+ pre-built integrations, No vendor lock-ins, All your users, groups, and devices in one place, & Automated 1-click user onboarding and offboarding.
The pricing for Workforce Identity Products plans starts at $2 per month/per user & goes up to $11 per user/per month. Plans after $4 offer between 50 workflows to unlimited workflows. The Advanced Server Access starts at $15 per server/per month.
The Customer Identity Cloud has three major plans, enterprise, B2B & B2C. The pricing for enterprise-level plans is quotation based, for the B2B plan the pricing ranges between $23 to $240, & B2C plan pricing ranges between $130 to $800.
For Detailed pricing, visit Okta pricing page.
Okta Pros & Cons
| Pros 👍 | Cons 👎 |
|---|---|
| Fast & Responsive | Lack of customisation |
| Instant notifications | Less responsive |
| Responsive customer support | Buggy mobile app |
SpotSaaS has rated and scored Okta at 9.8 out of 10. Check more about the product Here.
OneLogin
With the help of OneLogin, a cloud identity and access management system, businesses can safeguard all apps for their users across all platforms.
The identity base for creating safe, scalable, and clever trusted experiences that link people with technology is the OneLogin Trusted Experience Platform. Manage employee and customer digital identities easily with OneLogin so that users can concentrate on what’s important—expanding their businesses.
They can instantly connect all of their applications with OneLogin’s comprehensive solution, make use of its unique machine learning to discover and evaluate potential threats and take swift action using its contextual authentication requirements.
Millions of people use OneLogin at more than 2000 organizations across more than 44 nations. Thomas B. Pedersen and Christian Pedersen created OneLogin in 2009; its headquarters are in San Francisco.

OneLogin Features
- Compliance Management
- Access Request Management
- Account Management
- Password Management
- Multi-factor Authentication
- Role Management
- Single Sign-On (SSO)
- Social Sign On
- API Access Management
- Integrate With Tools
OneLogin Pricing
OneLogin offers a free trial for 30 days. The free trial includes Cloud Directory, Desktop + Mobile SSO, Advanced Password Reset, Custom Reports, Security Policies, MFA, and VPN integration.
The company offers 2 paid plans-
The Advanced plan includes: Single Sign-On (SSO), Advanced Directory, and Multi-Factor Authentication (MFA) and is priced at $4 per user/month.
The Professional plan includes: All Advanced Bundle Products, Identity Lifecycle Management, HR Driven Identity and is priced at $8 per user/month.
For Detailed pricing, visit OneLogin pricing page.
OneLogin Pros & Cons
| Pros 👍 | Cons 👎 |
|---|---|
| Integrate well with other tools | Lacks good On-Boarding and Off-Boarding Workflows |
| Simplified automation | Multiple password creation is required |
| Responsive customer support |
SpotSaaS has rated and scored OneLogin at 9.2 out of 10. Check out the product here.
Conclusion
In conclusion, Identity and Access Management (IAM) systems are essential for assuring modern enterprises’ compliance and safety. IAM systems assist enterprises in reducing the risks related to cyber attacks, data breaches, and legal infractions by centralizing and automating the management of user identities and permissions.
However, putting into practice an efficient IAM solution is a difficult process that needs significant forethought and planning. It is crucial to pick the appropriate IAM solutions, ensure they are properly set, and keep them up to date to satisfy your organization’s unique demands and requirements.
You can effectively deploy and administer IAM technologies in your organization by following the instructions in this comprehensive blog, and you’ll reap the rewards of improved security, effectiveness, and compliance.
Want to learn about more top IAM tools? Here’s a detailed blog on the same by team SpotSaaS.
The 5 Top Identity and Access Management (IAM) Tools
FAQs
What is IAM?
Identity and access management (IAM) is the practice that ensures the right individuals get access to the right resources at the right times and for the right reasons. It helps businesses to protect data & resources within & outside the business.
What is the core component of IAM?
IAM systems typically include several components, which may include:
User Directories
Authentication systems
Authorization systems
Password management systems
Single sign-on (SSO) systems
Access governance systems
What does identity and access management do?
Protect organizations’ data & resources from reaching the wrong hands & streamline business operations by providing required data access to a professional with access to the same.
Read More:
Resource Management Software: A detailed guide on how to use
The 6 Best Document Management Software for Enhanced Collaboration and Security